
Data protection with Microsoft 365
Editor’s note: This article was published in 2019 and has been updated for accuracy and comprehensiveness as of January 2021.
Recent research by the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency revealed that many Office 365 tenants in the United States are vulnerable to attacks and exploits.
Misconfigured networks are the reason for these vulnerabilities. Office 365 isn’t an inherently risky platform. Just like any other technology, it’s only as secure as you are willing to make it. Data protection is important, and Microsoft 365 gives you the tools to improve it.
In fact, there are now so many security tools available from Microsoft that it can be difficult to know where to start. While multi-factor authentication is an excellent start, it is not enough on its own. Keep reading to learn about five security enhancements you should be making with your investment in Microsoft 365 and any other cloud apps.
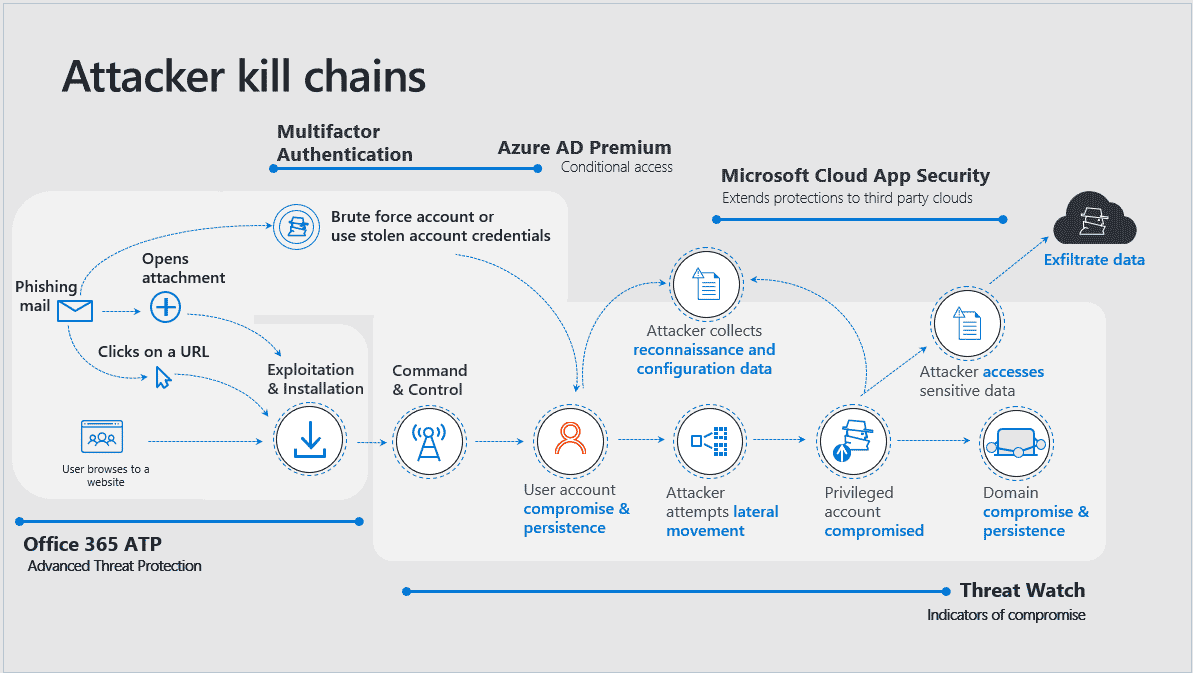
1. Enable Multifactor Authentication (AND disable basic)
Compromised passwords are still the number one attack vector hackers use to gain access to resources, exfiltrate data, and execute destructive processes like ransomware. Multifactor Authentication (MFA) is the number one thing you can do to improve your company’s data protection in the cloud.
MFA enforces an additional step to prove identity before gaining access to resources and data. The easiest and most secure way to accomplish this is using the Microsoft Authenticator app for iOS and Android, which will prompt users to click “Approve” or “Deny” on their mobile device when they authenticate.
Beware: you could be vulnerable to brute force attacks if you forget to disable basic authentication when you enable MFA. This is because basic authentication does not support MFA. Microsoft now provides a free baseline policy that will do this for you, but it is not turned on by default. According to Microsoft, disabling basic authentication will reduce your risk of compromise by more than 66 percent, increasing your data protection.
2. Configure Conditional Access
One of the biggest barriers to adopting new security controls is the pain of change. With conditional access, you can reduce user frustration while improving security. For example, in high-risk situations, you can enforce MFA. Or, If you find a user’s credentials on the dark web, you can force a password reset.
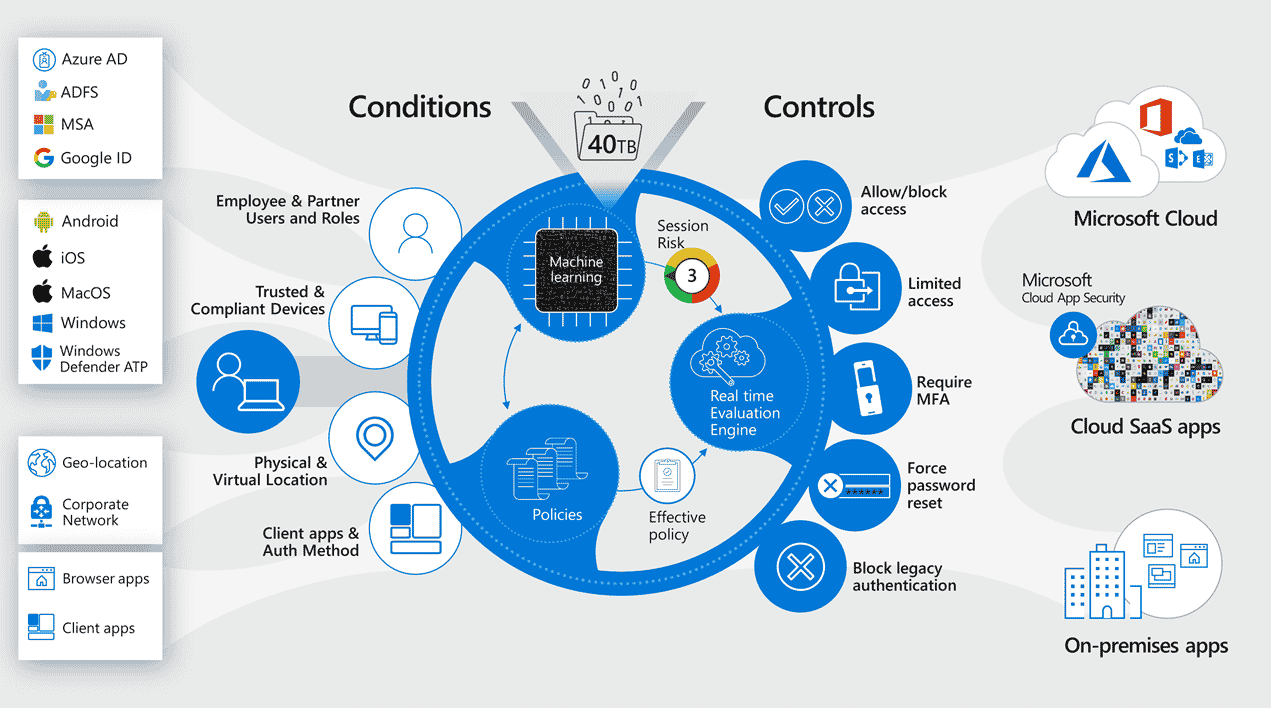
To take it even further, you can tailor a different experience to the end-user if they attempt to access resources from a BYOD or unmanaged device, versus one that is corporate-owned and corporate-managed.
3. Data protection from the unknown
Office 365 Advanced Threat Protection (ATP) is a good way to start defending against phishing attacks and zero-day malware. It includes AI-based anti-malware detection for attachments, protection against malicious links embedded in email and documents, and anti-phishing and anti-impersonation intelligence that will warn protected end-users against suspicious emails.
4. Modernize Device Management
In a modern framework, we want to manage ALL devices using the same tools. And we want those tools to work from anywhere. With Microsoft 365, you can actually turn users’ devices into part of their identities. This means the device can be leveraged as a condition to grant, limit or deny access to resources. To reinforce data protection and improve user experience, we can integrate conditional access to eliminate excess password and MFA prompts.
When it comes to managing employee-owned devices, an alternative to full mobile device management (MDM) is mobile application management (MAM). This means enforcing the use of Microsoft applications such as Outlook, Teams, and OneDrive for iOS and Android users.
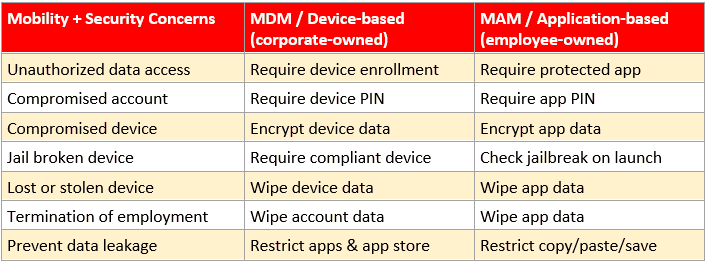
Using these applications ensures the best experience with cloud-hosted email and files for end-users while preventing the movement of data to other apps or locations. Additionally, corporate data can be wiped from the device without disturbing an exiting employee’s personal data. To pick up these capabilities, implement Microsoft Intune available in the Microsoft 365 Business SKU.
5. Manage third-party applications
Managing multiple identities and passwords is hard. Microsoft 365 allows third-party applications into the Azure Active Directory so that logins can be eliminated. Businesses can also control access while gaining more visibility into those other cloud environments. This can also pair with advanced security features and data protection like:
- MFA
- Blocking downloads on unmanaged devices
- Conditional access
While Office 365 and Microsoft 365 Business plans will allow you to set up single sign-on to third-party cloud apps, you will derive the most benefit from this arrangement with the addition of Azure AD Premium, and Microsoft Cloud App Security.
Conclusion
Microsoft 365 provides many tools to help you learn what data you need to protect because you cannot protect what you do not know you have. Once that relevant data is gathered, SUCCESS can help you create protections through Microsoft 365 such as:
- Enforcing device compliance
- Blocking risky sign-in attempts
- Limiting access under specific conditions
- Alerting you to unusual activity
- Enforcing automated remediation, via policy
Do you have visibility into when your company is being targeted? Or when a risky event is taking place? If you can’t answer this confidently, then you need to be talking to your fully-equipped team at SUCCESS about improving your security posture in the cloud.
Contact SUCCESS at (763) 593-3000 if you have questions, or if you are ready to continue on the secure cloud journey.